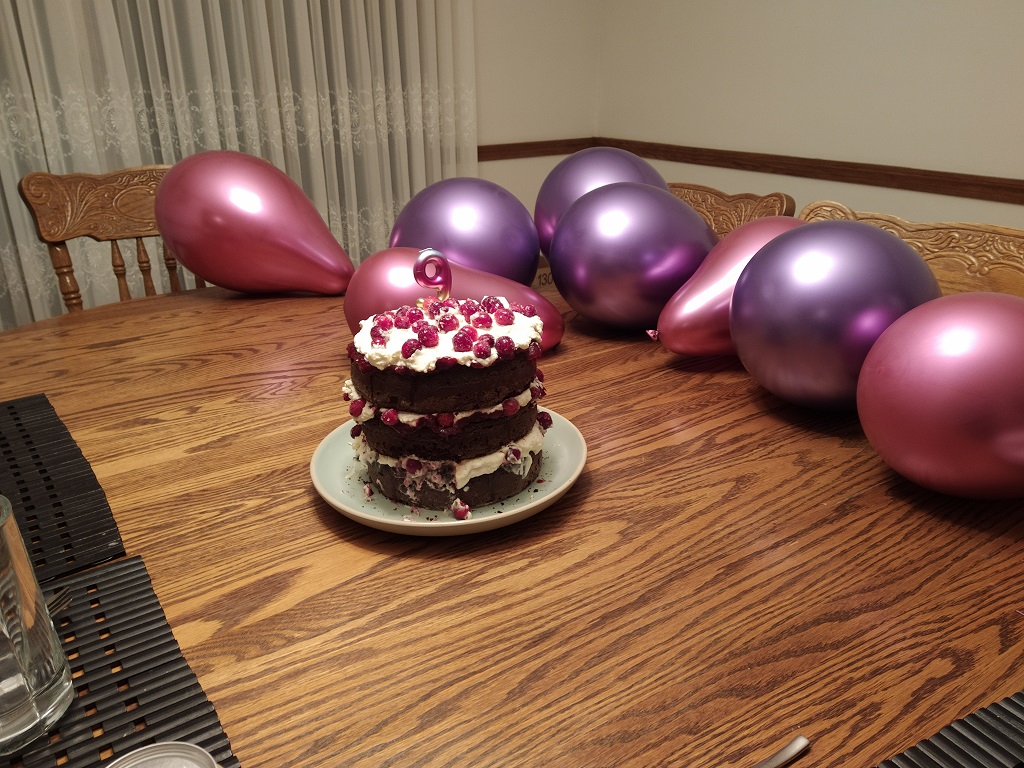I’ve started making a new blanket using Bernat blanket yarn. The pattern alternates between half double stitches and triple stitches (although the first and last row are half double stitches).
On The Coup
We have reached a point where Dick Cheney is making an appearance on the House floor to support his daughter in her belief that attempting a coup is, well, not the pinnacle of American democracy?!?
For a long time, I absolutely believed both parties in the United States thought they were trying to do the right thing for the country. I remember going to a rally against privatizing social security — one of Bush 2’s early initiatives. The local NPR station had a reporter meandering around looking for younger people to interview — looking, specifically, for people who were worried that their retirement wouldn’t include social security. I, on the other hand, knew the history of the social security system. It was started after people lost huge sums of money — some more money than they had (thanks, leveraged buying) in a stock market downturn. The basis of social security is, essentially, that you can realize greater returns in riskier investments. But you can also lose everything in riskier investments, and this program is the backstop against “losing everything”. In that context, how is it reasonable to consider allowing individuals to direct social security funds into riskier investments because they might be able to outperform government bonds?!? But … I got it. We were decades away from the great depression, and years before the crash of 2008/2009. Most people had only experienced upward movement in the market. And the question at hand was really “is this form of insurance against stock market crashes still worth it?”. I could look at pretty much any political debate and understand how both sides had a coherent argument and viewed their position as The Right Thing To Do.
Maybe that’s still true today — but it seems like conservatives have become more adamant about forcing their will on the nation to retain power. To make money. We watched a dude on MSNBC basically admit to participating in a coup attempt not because he was ashamed of his actions. Not because he wanted to make sure everyone understood what exactly happened. But because he wanted to sell his new book. Well, mission accomplished (I guess). He’s managed to get his name out there & we all know he’s got a book. Liberals can buy it to prove there was a coup and conservatives can buy it to see “the receipts” on stealing an election. (Receipts which have been promised on multiple occasions but which have never been produced).
I’m still hopeful that the end result of this mess is a viable third (fourth, or even fifth) party. Maybe some actual fiscal conservatives (not deficit spending dumped into the military industrial complex v/s tax for domestic spending). Some democratic socialist party that makes Bernie seem pretty middle-of-the-road.
Anya’s 9th Birthday Cake
This year, Anya wanted a cranberry black forest cake. Which I didn’t really realize was a thing, but I found a recipe online. I used maple whipped cream between layers with maple glazed whole cranberries. It was tasty, but a little dry. If I were making it again, I would either soak it in some cranberry juice or some other liquid.
Still tasty!
Ducks Growing Up
Today was a great day to be a duck again — warm-ish weather, the pond isn’t frozen over. So they’ve been enjoying splashing and swimming. But, this morning, I could only count five ducks in the pond. Checked around the yard, but I didn’t see the other duck. Then a ducky head popped up from underwater and … well, it looked like one duck was trying to drown another duck! Then something I read in a duck forum popped into my head — ducks mating can seem like the drake is trying to kill the female. Or it could look like the drake is trying to drown the female (which … IMO, seems a lot like “trying to kill”. So I’m not sure what exactly the person was trying to convey there!). Our ducks are about five months old and, evidently, have matured enough to start mating. Hopefully, we’ll be able to hatch some new ducks in the spring!
ElasticSearch 7.7.0 Log4J Vulnerability Remediation
We are a little stuck with our ElasticSearch implementation — we need the OpenDistro authentication, so either need to buy newer ElasticSearch or move to OpenSearch. That’s an ongoing project, but it won’t be accomplished in a timely fashion to address these log4j issues.
To address the existing Log4J issues in ElasticSearch as well as, evidently, another challenge that meant a new log4j build over the weekend, I am manually replacing the Log4j jar files for ElasticSearch 7.7.0, OpenDistro Security, and the S3 backup plugin. The 2.11.1 version that was bundled with the distribution can be replaced with the 2.17.0 release from Dec 18th.
The new JARs can be downloaded from Maven Repo at:
https://mvnrepository.com/artifact/org.apache.logging.log4j/log4j-core/
https://mvnrepository.com/artifact/org.apache.logging.log4j/log4j-api/
https://mvnrepository.com/artifact/org.apache.logging.log4j/log4j-slf4j-impl/
https://mvnrepository.com/artifact/org.apache.logging.log4j/log4j-1.2-api/
To upgrade just log4j, the following script is run … well first allocation is disabled:
# Stuff to stop/start routing in Kibana
POST /_flush/synced
PUT /_cluster/settings
{ "transient" : { "cluster.routing.allocation.enable": "none" } }
Then the script is run:
export l4jver=2.17.0
systemctl stop elasticsearch
# Remove old jars
rm --interactive=never /opt/elk/elasticsearch/lib/log4j-api-*.jar
rm --interactive=never /opt/elk/elasticsearch/lib/log4j-core-*.jar
rm --interactive=never /opt/elk/elasticsearch/modules/x-pack-identity-provider/log4j-slf4j-impl-*.jar
rm --interactive=never /opt/elk/elasticsearch/modules/x-pack-security/log4j-slf4j-impl-*.jar
rm --interactive=never /opt/elk/elasticsearch/plugins/opendistro_security/log4j-slf4j-impl-*.jar
rm --interactive=never /opt/elk/elasticsearch/modules/x-pack-core/log4j-1.2-api-*.jar
rm --interactive=never /opt/elk/elasticsearch/plugins/repository-s3/log4j-1.2-api-*.jar
# Copy in upgraded jars
cp /tmp/log4j-api-$l4jver*.jar /opt/elk/elasticsearch/lib/
cp /tmp/log4j-core-$l4jver*.jar /opt/elk/elasticsearch/lib/
cp /tmp/log4j-slf4j-impl-$l4jver*.jar /opt/elk/elasticsearch/modules/x-pack-identity-provider/
cp /tmp/log4j-slf4j-impl-$l4jver*.jar /opt/elk/elasticsearch/modules/x-pack-security/
cp /tmp/log4j-slf4j-impl-$l4jver*.jar /opt/elk/elasticsearch/plugins/opendistro_security/
cp /tmp/log4j-1.2-api-$l4jver*.jar /opt/elk/elasticsearch/modules/x-pack-core/
cp /tmp/log4j-1.2-api-$l4jver*.jar /opt/elk/elasticsearch/plugins/repository-s3/
# Fix permissions
chown elkadmin:elkadmin /opt/elk/elasticsearch/lib/log4j*
chown elkadmin:elkadmin /opt/elk/elasticsearch/modules/x-pack-core/log4j*
chown elkadmin:elkadmin /opt/elk/elasticsearch/modules/x-pack-identity-provider/log4j*
chown elkadmin:elkadmin /opt/elk/elasticsearch/modules/x-pack-security/log4j*
chown elkadmin:elkadmin /opt/elk/elasticsearch/plugins/repository-s3/log4j*
chown elkadmin:elkadmin /opt/elk/elasticsearch/plugins/opendistro_security/log4j*
systemctl start elasticsearch
# Clean up temp files
rm /tmp/log4j*
And finally routing is re-enabled:
PUT /_cluster/settings
{ "transient" : { "cluster.routing.allocation.enable" : "all" } }
Linux: Copying Files and Preserving Timestamps
To copy files and keep the original timestamp, use
cp --preserve=timestamps /path/to/source.txt /path/to/destination.txt
Home Automation and Gardening
Something like 20 years ago, I tried to grow a plumeria flower in my apartment. I had a broad-spectrum light, plenty of heat, and plenty of humidity. But getting the light turned on and off at the right times wasn’t easy (especially if I was at work all day!).
This seems like a really good use for home automation — our home automation system tracks the sunrise and sunset times for our zip code. It’s possible to essentially cron “stuff” off of these times — e.g. get the birds ten minutes before sunset. I could easily track sunrise and sunset in Honolulu then have my light turn on at sunrise (or first light) and off at sunset (or last light). Voila — “sunlight” that runs for the proper duration every day.
Nothing like a fish
I had an older friend explain why he was absolutely certain his wife and he were going to have a long, happy marriage (they’d been married for a few decades by this point, so he wasn’t speculating). They went on vacation to a small town to get married and honeymoon. Small enough town that the wedding license department and fishing license department (as well as all of the other government functions) were in the same place. Dude wanted to get a fishing license, so he offered to go get both. Shows up and gets his fishing license. Then asks about the wedding license. Government dude says the wedding license dude is on vacation today. Come back tomorrow. My friend asked if government dude could do it. Nope, cannot do it. Friend asked what if his girlfriend looked like a fish, was that close enough? They laughed, and government dude said both people need to be here anyway … so come back tomorrow, and bring her. We’ll get you sorted.
He goes back to their hotel, tells her they both need to be there, and that license dude wont be in the office until tomorrow. The next day, they head back. Dude and his girlfriend walk into the office, and government dude looks at them and says ‘you are wrong, she looks nothing like a fish!”. Future wife says “how about now” and makes her best fish face. They all laugh.
He told me there’s nothing wrong with not wanting your spouse to make fun of your face. And there’s nothing wrong with joking around either. The problem is when the two people aren’t on the same page. They could still make it work, but the jokey partner is going to go through life having to curb their immediate impulse to turn something into a joke. Or the other partner is going through life being humiliated by someone who is supposed to love and support them.
Tar Quickref
Create a gzipped tar archive:
tar -czvf /path/to/file.tar.gz ./stuff-to-archive
List contents of a gzipped tar archive:
tar -ztvf file.tar.gz
Extract contents of a gzipped tar archive:
tar -zxvf file.tar.gz
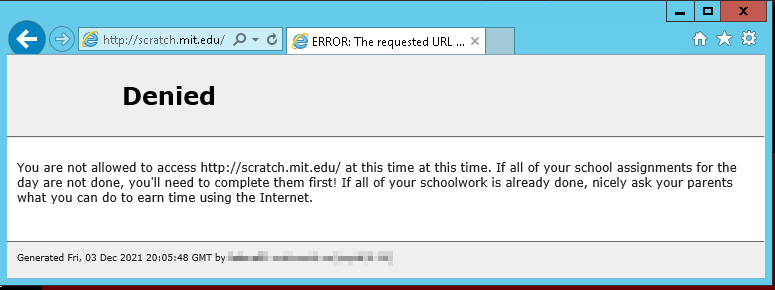
Squid Custom Error
We’ve been having a challenge with Anya getting her school work completed. Part of the problem is the school’s own fault — they provide a site where kids are encouraged to read, but don’t provide any way to ensure this reading is done after classwork has been completed. But, even if that site didn’t exist … the Internet has all sorts of fun ways you can find to waste some time.
So her computer now routes through my proxy server. I’d set up a squid server so *I* could use the Internet unfettered whilst VPN’d in to work. It’s really annoying to get told you’re a naughty hacker every time you want to see some code example on StackOverflow!
While I didn’t really care about the default messages for my use (nor did I actually block anything for it to matter), I want Anya to be able to differentiate between “technical problem” the site didn’t load and “you are not allowed to be using this site now” the site didn’t load. So I customized the Squid error message for access denied. This can quickly be done by editing /usr/share/squid/errors/en-us/ERR_ACCESS_DENIED (you’ll need to make a backup of your version & may need to replace the file when upgrading squid in the future).