Before upgrading to 8, you must be running at least version 7.17 … so I am first upgrading my ES7 to a new enough version that upgrading to ES8 is possible.
Environment
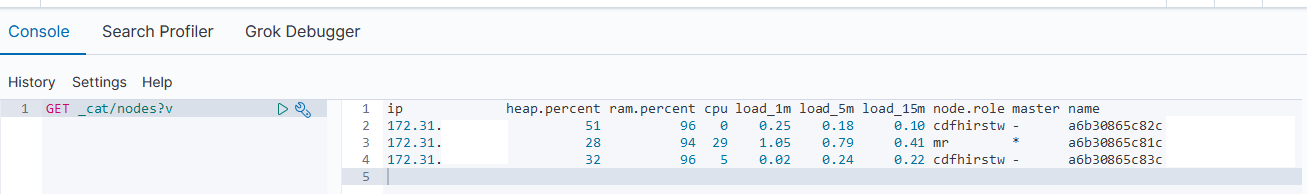
Not master eligible nodes:
a6b30865c82c.example.com
a6b30865c83c.example.com
Master eligible nodes:
a6b30865c81c.example.com
- Disable shard allocation
PUT _cluster/settings{ "persistent": { "cluster.routing.allocation.enable": "primaries" }}
- Stop non-essential indexing and flush
POST _flush/synced
- Upgrade the non-master eligible nodes first then the master-eligible nodes. One at a time, SSH to the host and upgrade ES
a. Stop ES
systemctl stop elasticsearch
b. Install the new RPM:
rpm --import https://artifacts.elastic.co/GPG-KEY-elasticsearch
wget https://artifacts.elastic.co/downloads/elasticsearch/elasticsearch-7.17.3-x86_64.rpm
wget https://artifacts.elastic.co/downloads/elasticsearch/elasticsearch-7.17.3-x86_64.rpm.sha512
shasum -a 512 -c elasticsearch-7.17.3-x86_64.rpm.sha512
![]()
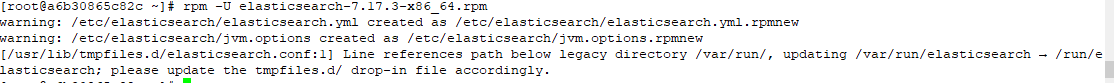
rpm -U elasticsearch-7.17.3-x86_64.rpm
c. Update configuration for new version
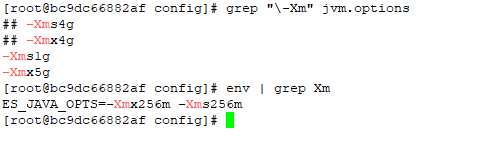
vi /usr/lib/tmpfiles.d/elasticsearch.conf
![]()
vi /etc/elasticsearch/elasticsearch.yml # Add the action.auto_create_index as required -- * for all, or you can restrict auto-creation to certain indices
d. Update unit file and start services
systemctl daemon-reload
systemctl enable elasticsearch
systemctl start elasticsearch.service
- On the Kibana server, upgrade Kibana to a matching version:systemctl stop kibana
wget https://artifacts.elastic.co/downloads/kibana/kibana-7.17.3-x86_64.rpm
rpm -U kibana-7.17.3-x86_64.rpm
sytemctl daemon-reload
systemctl enable kibana
systemctl start kibana - Access the Kibana console and ensure the upgraded node is back online
- Re-enable shard allocation
PUT _cluster/settings{"persistent": {"cluster.routing.allocation.enable": null }}