Your Cuyahoga County Library account can be used to gain free access to the electronic editions of a few national newspapers — including New York Times and Washington Post. You just have to use the links from https://cuyahogalibrary.org/read-watch-listen/digital-library/newsstand to get a few days of free access.
Author: Lisa
Kahtoola MicroSpikes
I picked up a pair of MicroSpikes and NanoSpikes at the end of last season as retailers were clearing out their winter gear. These are awesome for walking in the snow and ice — I wasn’t sliding around at all.
The negative five degree temps (negative thirty with windchill) taught me that I’m not quite done purchasing winter gear — my balaclava kept most of my face warm, but ski goggles for the little bit of skin around my eyes away from the blowing ice.
4K v/s NanoCell
We did a side-by-side comparison of the LG UQ75 and QNED80 — I was surprised at how different the picture was — there are so many more stars visible, and the background black space was much darker. Since both were basically the same price, the QNED was certainly a good purchase.
| UQ75 | QNED |
 |  |
Ash Kit
Accessing Records – Cuyahoga County Probate Court
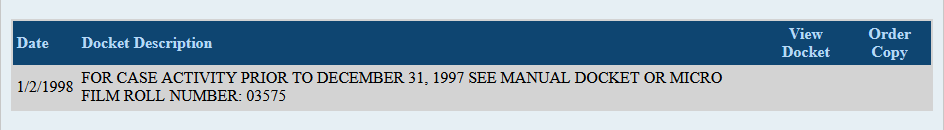
We went up to the County Courthouse today to view some old probate records — just like the recorders office, this is all stored seemingly forever and available to the public to review. There is a room where the microfiche is stored in cabinets.
Each drawer is full of boxes — when you search the Cuyahoga County probate court records, newer records have files in the “Docket” that you can view. Older cases don’t.
They do, however, contain a record that provides the film roll number.
And each file drawer has a list of numbers housed in the drawer — to find the film for this case, I needed to find the drawer with roll 03575
Voila — here’s the roll. Each box indicates the range of case numbers imaged onto the roll … I confirmed the case number I wanted was in that range.
They also have a film viewer computer — if you select the type of film, the screen will give you a little animated video with instructions on loading the film. Look for that in the lower right-hand corner of the screen.
Quick Python Bingo Caller
I keep re-writing the same quick script to implement a bingo “caller” so Anya and I can play a game … figured I’d save it somewhere and save a few minutes next time! We use more words than squares so not every word is on both boards, but you can shorten the list to 24 and just put the words in different squares on each board.
import random
# initializing the word list -- 24 words for the 24 squares but we play with more words than squares!
wordList = ["Hypothesis", "Observation", "Theory", "Variable", "Cat"
, "Fun", "Science", "Happy", "Dog", "Thyme"
, "Rosemary", "Sage", "Time", "Run", "Pot"
, "TV", "Rogue", "Smile", "Black", "Rock"
, "Ash", "Kitten", "Love", "Bingo (but not BINGO like somebody won!)",
"Mom", "Dad", "Anya", "Wood", "Trail", "Tail", "Star"]
# shuffling word list
random.shuffle(wordList)
i = 0
while i < len(wordList):
print(wordList[i])
i += 1
x= input()
Windows Admin Center – Changing the Port
Where I work, the “OS Support” and “Application Support” functions are different verticals. Sometimes what constitutes an “OS” and what constitutes an “application” is nebulous. In this case, we needed to install a web-based application but found TCP port 443 was already bound to Windows. Unfortunately, the OS support group disclaims any ownership of “Windows Admin Center” and told me I was welcome to fix it myself. So … oddly, there isn’t any easily located configuration for this thing. You have to go through the add/remove programs and modify the installation of Windows Admin Center.
Select “Change”
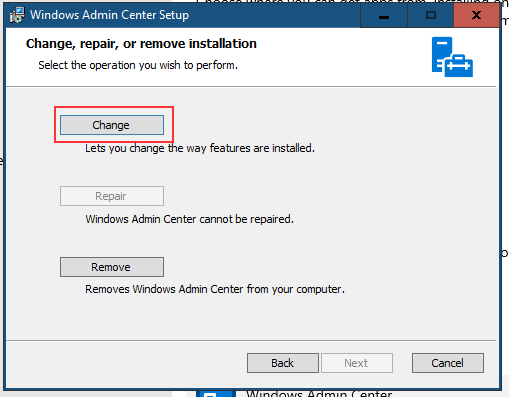
You will get the configuration panel — here, you can specify a different port for the Admin Center.
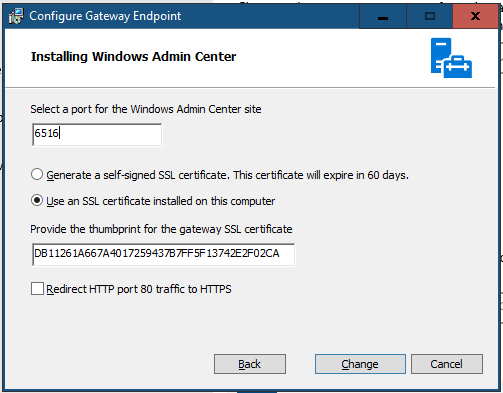
Let the installer complete …
Voila — not using port 443!
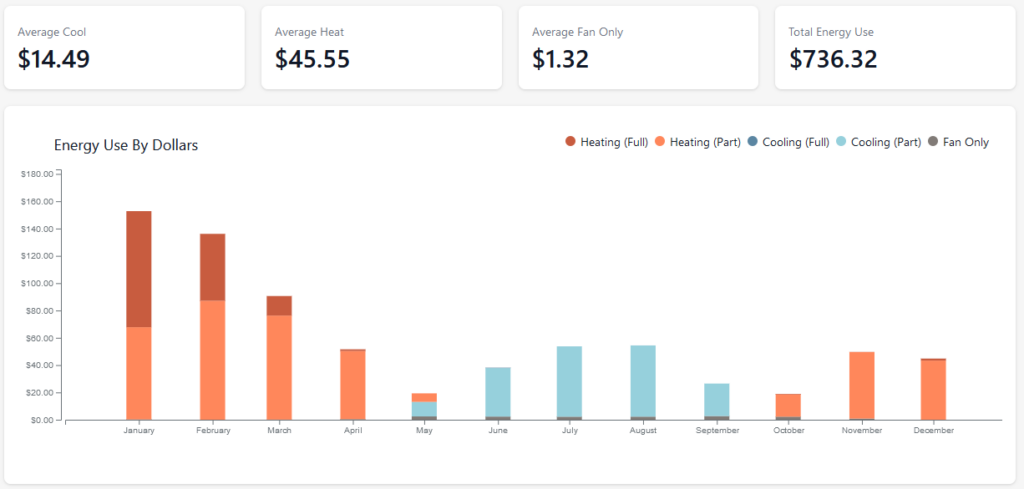
Geothermal Energy Use — Multi-Year Analysis
I’m starting to look at some year-long roll-ups of our energy usage – the geothermal is running just around $700 a year to both heat and cool the house to really comfortable levels. Since we had paid $800 to fill up the propane task that lasted maybe a month, this is an incredible saving compared to the propane heater.
2020 Energy Usage
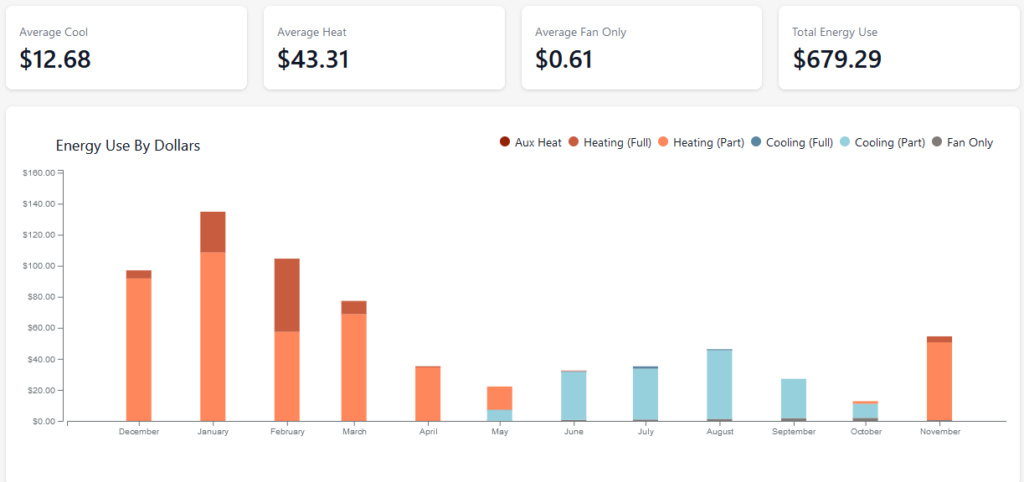
2021 Energy Usage
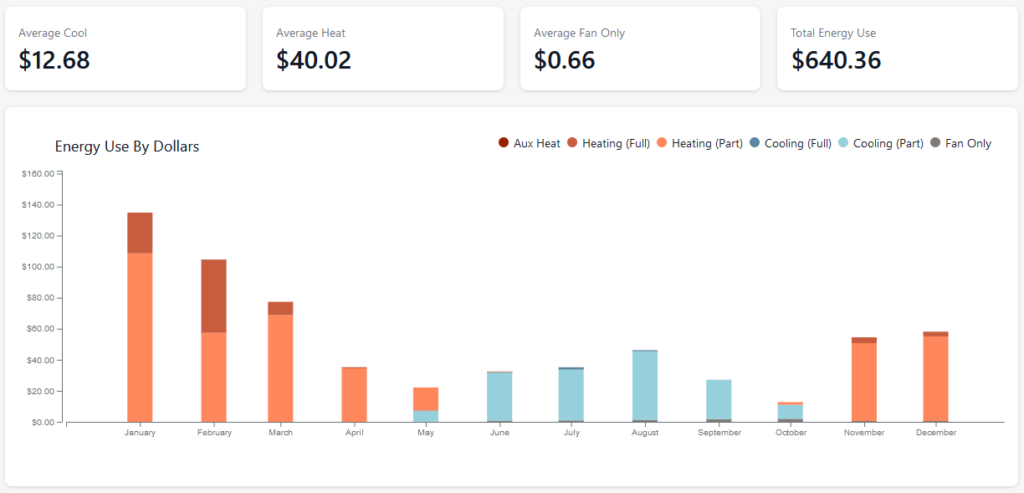
2022 Energy Usage
Planting Garlic
I planted our garlic today — an assortment of varieties filling one of the raised beds.
I only added about an inch of mulch to the bed. The garlic I planted last year never formed heads — we had lots of green leaves, beautiful scapes that we harvested quickly … but no garlic bulbs! Evidently garlic cloves need exposure to cold temperatures in order to form bulbs. You can actually mulch them too well! Hopefully I’ve got enough mulch to suppress weeds and retain moisture but not so much mulch that the cloves are too toasty this winter. 
Turkey Pot Pies
I wanted to use the left-over turkey from Thanksgiving to make some quick(ish) pre-cooked freezer meals. Turkey pot pies sounded like a neat idea — make a couple batches of pie dough, saute a bunch of veggies, add diced turkey, and turn stock make with the bones into fresh gravy.
The first step was to dice up all of the left-over turkey — then put the bones along with some salt, onion, and garlic cloves in a pressure cooker to make a stock. I used a combination of roux and corn starch to thicken the stock into a gravy.
I diced carrots, broccoli, onion, garlic, and green beans and sauteed it all. Then mixed in corn kernels and the diced turkey.

After stirring in the gravy, I’ve got turkey pot pie filling.

I assembled a large pie for dinner.

Since the filling is wet, I blind baked the bottom crust for twenty minutes then filled the pie and added a top crust. The large one for dinner went into the oven. The six small pies were topped and put into the freezer to firm up.

Once everything was frozen, I used the vacuum sealer to package up my pies. Since I have ceramic mini pie plates, I need to take these out of the freezer and sit the package in a water bath to warm up the ceramic. Then bake at 350 F for about an hour for a simple (but not really quick) meal.

They turned out well — the extra baking of the mini pies made a nicely caramelized and crunch bottom crust. For next time, gravy absorbs into everything, so I need more gravy. And I think it would be a lot easier to have one larger pie instead of the three individual ones. Just need to pick up a few stainless steel deep-dish pie plates so I have something that can actually go from the freezer to oven directly.