Facebook is getting a lot of attention for the information it gathers and how well it secures personal data you provide. We should look just as intently at other companies. Some provide services to individuals in exchange for advertising data, and some provide advertising targeting services without offering anything to the individuals being tracked.
LinkedIn — Maybe because “professional” information about oneself does not feel as private as that which is shared on Facebook, LinkedIn gets overlooked a bit. The companies I’ve worked for and titles I’ve held almost seem like public records. You can download a copy of “your data” (like Facebook, this is not apt to contain meta-data they’ve gathered regarding you – just data you have submitted to the site). In your settings, use the privacy tab and scroll down to “How LinkedIn uses your data” – the first selection is to download your data.
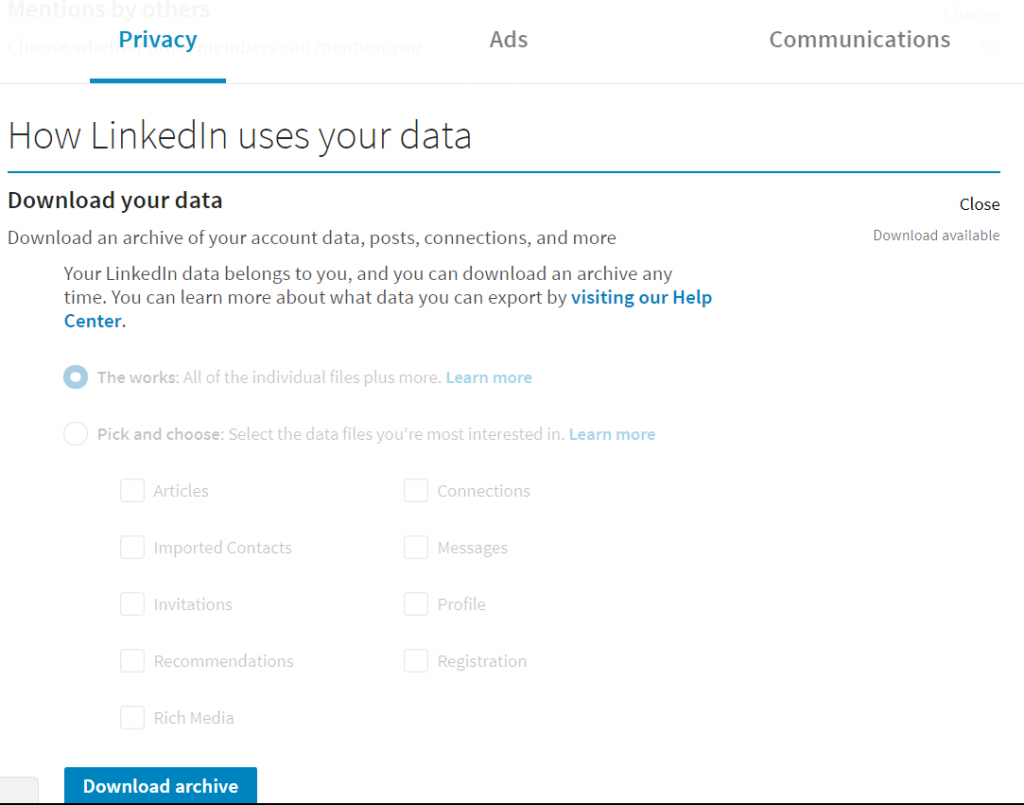
Nothing stunning – a list of contacts, my various employers and titles. But LinkedIn is trying to slurp in my entire contact list, maintain a web of people who know people, and allow advertisers to target users. There’s a whole tab apart from your privacy settings to control how your data is used for advertising purposes. “Advertisers” seem to be corporate hiring agents and recruiters, so this marketing is not always mentally classified as “advertising”.
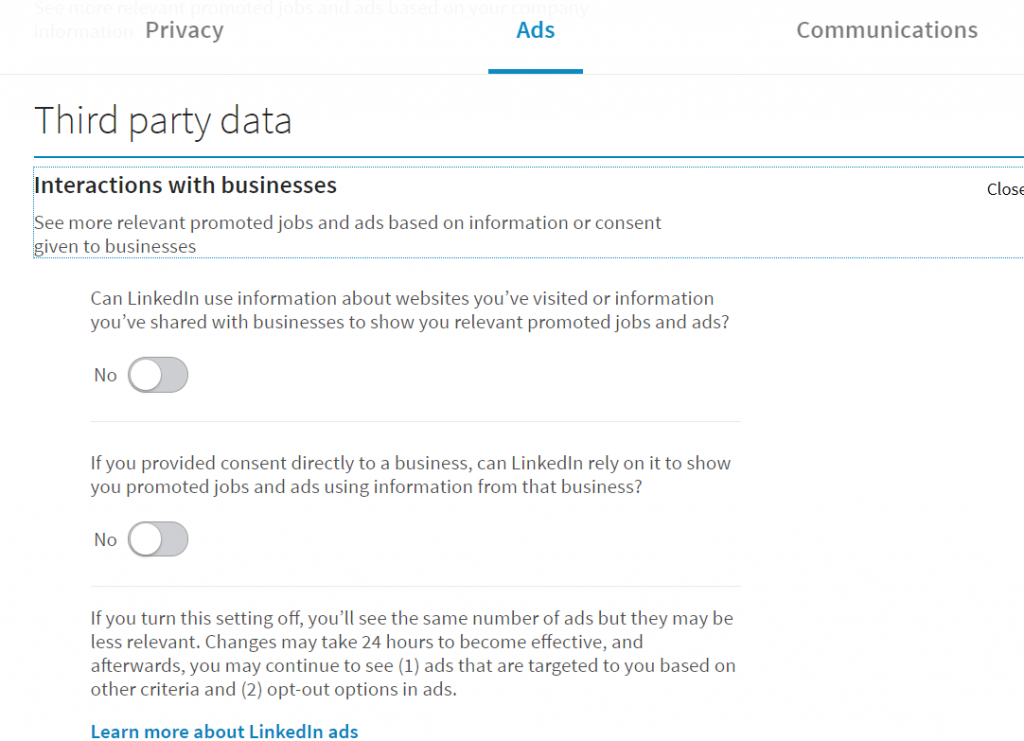
LinkedIn also has a setting which allows you to opt-out (mine was on, and I’ve never opted in so I assume it is an opt-out deal) of having some of your data made available to third parties for policy and academic research.
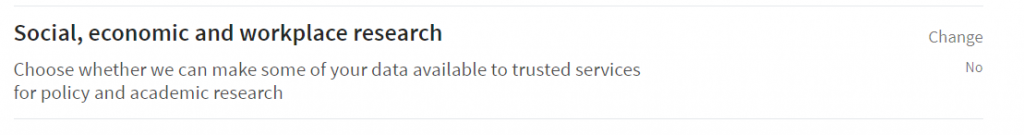
And remember that Facebook Pixel? LinkedIn wants to track information about “websites you’ve visited” and “information you’ve shared with businesses” to show you more relevant jobs and ads.
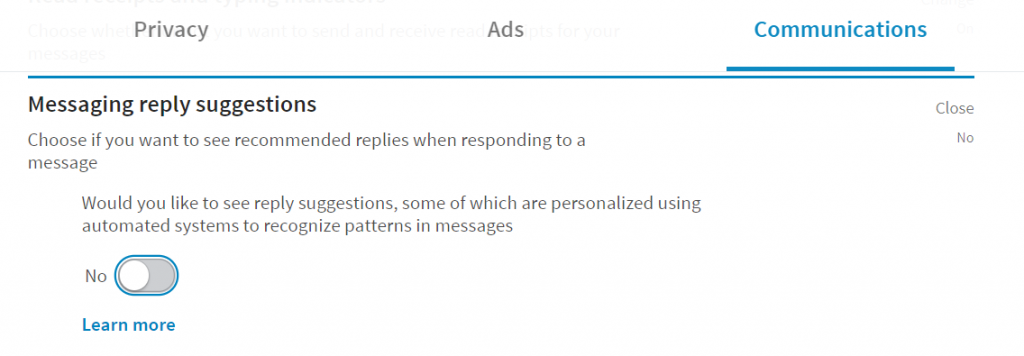
Beyond the data feeling less private, having high-paying jobs that need my exact skill set and tend to hire people with my browsing history … well, that feels like a score compared to Facebook’s ad trying to coerce me once again to buy a pair of roller skates I already decided wouldn’t work for my daughter. Even if you’re not actively interested in changing jobs, it is nice to feel wanted. But that’s a nice veneer to data hording, analysis, and target marketing. They’ve even got a peculiar setting under the “Communications” tab that wants to use algorithms to analyze your messages to formulate suggested replies. This too seems to be an opt-out setting.
Google — no one uses Google+ (pity, that) but Google amasses information from searches, e-mails, Hangouts, Android phones. You can request an archive of your data through https://takeout.google.com — it takes a long time for the archive to be built, and it was an incredible amount of data. A few +1s from mis-clicks that there is no immediately obvious way to delete. “Bookmarks” that all appear to be map locations. A calendar that apparently was syncing with my home server back in 2009 since that’s the create date on all of the items. A whole folder for Chrome with 75 meg of browsing history and another meg of bookmarks (a meg of text is a *lot* of data, but I *love* that my bookmarks sync between devices). A handful of contacts that I assume my husband created in our shared account. The totality of every conversation I’ve ever had in Hangouts. Some Google Keep notes that I also assume are my husband’s from our shared account. My entire GMail mailbox, which is an obvious data source. The very tiny set of profile data I actually shared with Google.
Hell, Google has years worth of location data that I guess comes from my phone (it’s got fairly accurate lat/long coordinates, so GPS is the likely source). Following Google’s directions to delete the data didn’t work either (on the map, hit the hamburger menu then scroll ALL THE WAY DOWN to the ‘history’ selection”. Google both claims to have no history data for me and has 423 places on my timeline. Sooo, yeah, that would be history data. I finally managed to delete the stuff through my phone. There is a “Google Settings” app. Select “Location” from it, then “Google Location History”. There is a “Manage Activities” selection (use Google Maps to open it). Confirm you don’t want to use location history because, of course, it asks you to turn it on. Then use the hamburger menu button and select “Settings”. Waaay down at the bottom, there’s an option to delete all history or a date range of history. A couple of warnings later, the timeline map shows no data.
Then there are the photos. Gig after gig of photos. I had an Android phone that went into a reboot loop. I spent a few days wiping and reloading my phone, then failed back to an old phone. One of those iterations, evidently, slurped up all of the photos on my SD card because companies *want* your data. So the initial phone setup pushes you to backup your data, sync up your media, and generally upload ‘stuff’. One erroneous click and they’ve got metadata they’ll be able to keep forever. And there’s no readily apparent way to delete everything at once either. I’ve spent days on the web site deleting a couple hundred photos at a time. Not fun. Click the first picture, scroll down a bit, hold shift and click another picture. If you’re lucky, you didn’t select more than whatever the limit is (guessing 500) and you’ll get “389 Selected” in the upper left hand corner. At which point, you can click the delete and remove that chunk of photos. If you are not lucky, you get “2 Selected” and have to try again.
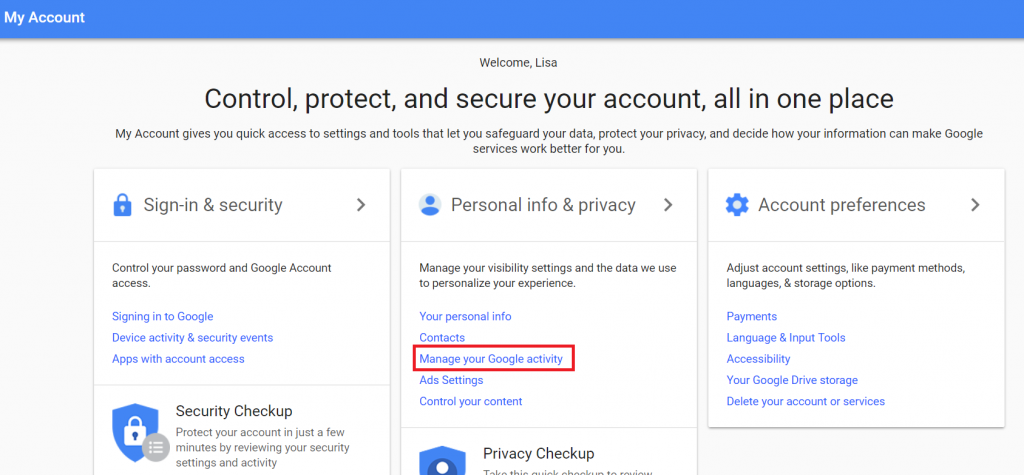
Ceasing data collection is much easier than removing data they’ve already grabbed. From your account settings, elect to “Manage your Google activity”. Then go into “Go To Activity Controls” and turn off (well, pause) whatever you want to turn off.
And I assume any bucket into which they’ve placed you based on previously gathered information will be retained even if you’ve deleted the underlying data.