On the most recent iteration of Windows (20H2 build 19042.1052) and Docker Desktop (20.10.7 built Wed Jun 2 11:54:58 2021), I found myself unable to launch my Oracle container. The error indicated that the binding was forbidden.
C:\WINDOWS\system32>docker start oracleDB
Error response from daemon: Ports are not available: listen tcp 0.0.0.0:1521: bind: An attempt was made to access a socket in a way forbidden by its access permissions.
Error: failed to start containers: oracleDB
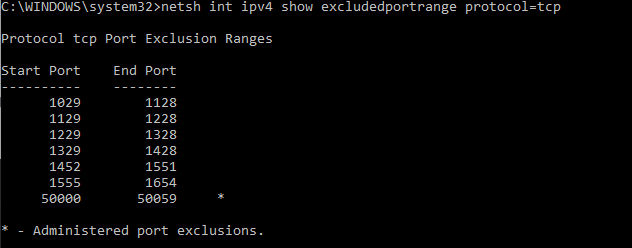
Forbidden by whom?! Windows, it seems. Checking excluded ports using netsh:
netsh int ipv4 show excludedportrange protocol=tcpShows that there are all sorts of ports being forbidden — Hyper-V is grabbing a lot of ports when it starts. To avoid that, you’ve got to add a manual excluded port for the one you want to use.
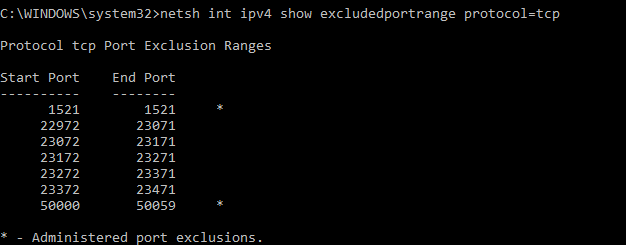
To reserve the port for your own use, disable Hyper-V (reboot), add a port exclusion, and enable Hyper-V (reboot)
REM Disable Hyper-V dism.exe /Online /Disable-Feature:Microsoft-Hyper-V REM REBOOT ... then add an exclusion for the Oracle DB Port netsh int ipv4 add excludedportrange protocol=tcp startport=1521 numberofports=1 dism.exe /Online /Enable-Feature:Microsoft-Hyper-V /All REM REBOOT again
Now 1521 is reserved for Oracle